Table of contents
Summary:
One of the most lethal and prevalent attack vectors in 2023 is still misconfiguration which happens due to human error. With the rapid growth of organizations and agility provided by Cloud Service Providers more and more organizations adopting the cloud.
Cloud service providers provide us with tools and services to manage the cloud configuration, but with rapid innovation, cloud providers add new functionality that adds to the complexity.
In this article, we will discuss the misconfiguration, the businesses affected due to misconfiguration, and how we can avoid misconfiguration.
Why should organizations care about Misconfiguration?
According to a report published by Gartner through 2025, almost 90% of organizations that will fail to control the public cloud will end up sharing sensitive data.
And, through 2025, 99% of cloud security failures will be the customer’s fault.
What is Misconfiguration?
Cloud Misconfiguration is configuration loopholes that exist in your infrastructure design, infrastructure services, and components. These loopholes can result from accidentally implementing security or configuration measures that provide unauthorized access to your resources.
Common misconfigured services that are not limited to security groups, access control lists, API Gateways, IDS, Web Application firewalls, virtual machines, weak usernames, password policies, storage access, unused open ports, and different cloud services.
Business Affected due Misconfiguration Attacks:
Verizon: In 2017, a security researcher discovered that millions of Verizon customer records were exposed due to a misconfigured Amazon S3 bucket. The data included names, addresses, phone numbers, and account PINs.
US Army Intelligence and Security Command in November 2017, exposed several files because of S3 misconfiguration.
Accenture in Sept 2017, exposed authentication information including certificates, plaintext passwords, keys, and sensitive customer information. Reason for breach- S3 misconfiguration.
Deloitte suffered a data breach in 2017 due to a misconfiguration of an email server hosted on Microsoft's Azure cloud platform. The breach exposed sensitive client data, including email addresses, usernames, passwords, and even health information.
NASA was Exposed because of default authorization misconfiguration in the tool that they used to collaborate- JIRA.
How you can prevent misconfiguration in your organization?
Implementing education and training: By implementing education and training, you can ensure that all employees understand the importance of IT security and are equipped with the knowledge and skills to prevent misconfiguration.
Least Privilege: The principle of least privilege, you can help prevent misconfigurations by ensuring that users, processes, and systems only have the access they need to perform their tasks. This can also help reduce the risk of data breaches, system downtime, and other security incidents.
Monitoring and governance: By implementing effective monitoring and governance practices, organizations can help prevent misconfigurations and reduce the risk of security incidents. This can help ensure that IT systems are configured correctly and that they remain secure and resilient over time.
Encryption: It can be an important tool for preventing misconfigurations and protecting sensitive data. By implementing secure key management practices, using encryption to protect data in transit and at rest, complying with regulations and standards, and following best practices for secure configuration management, organizations can help prevent misconfigurations and reduce the risk of data breaches.
Event-Driven Security: Once an event has been detected it is important to resolve it, and event-driven security can be an effective approach for detecting and preventing misconfigurations in cloud environments. By using real-time monitoring, automated responses, contextual analysis, and integration with other security tools, organizations can help ensure that their cloud infrastructure remains secure and resilient over time.
Let's see how HBO uses event-driven security architecture!
HBO event-driven security with detection and remediation:
HBO Max implemented event-driven security for infrastructure running on aws. It uses event-driven security to detect, remediate, and modify resources that are configured improperly.
Architecture:
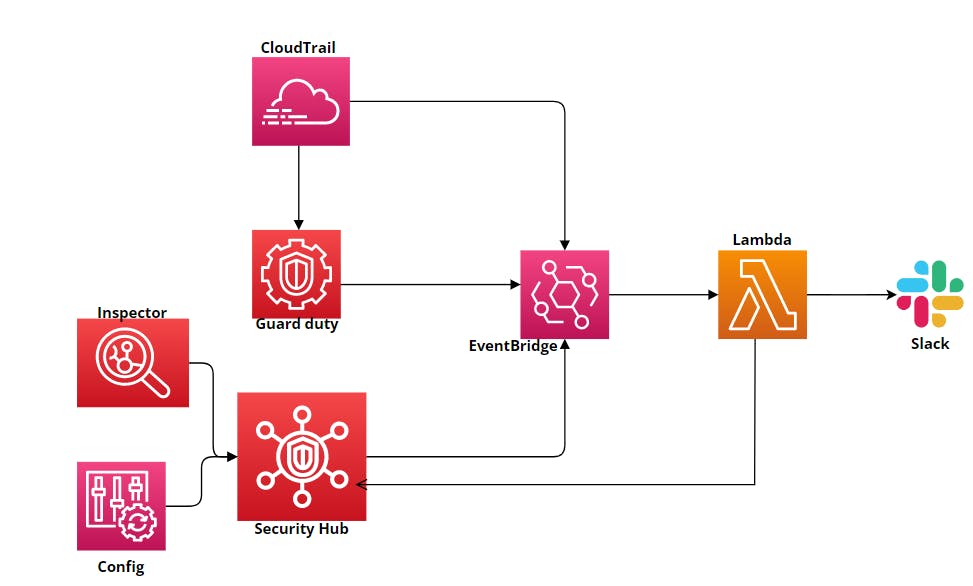
Architecture is broken down into two main segments Detection and Remediation.
Detection components:
CloudTrail: It records and stores activity logs for an AWS account. These logs contain information about API calls made within the AWS account, including the identity of the caller, the time of the call, and the parameters passed to the API. CloudTrail logs can be used to perform security analysis, resource change tracking, and compliance auditing. They can also help organizations troubleshoot operational issues by providing detailed information about AWS account activity.
Guard duty: It is a threat detection service provided by Amazon Web Services (AWS) that continuously monitors AWS accounts and workloads for malicious activity and unauthorized behavior. GuardDuty uses machine learning, anomaly detection, and integrated threat intelligence to analyze data from AWS CloudTrail logs, Amazon VPC Flow Logs, and DNS logs to identify potential security threats.
Security hub: where all the events from different security services are sources.
Remediation components:
Eventbridge and Lambda: all the events are published into the event bridge which triggers the lambda function. The lambda function runs a script that goes and remediates misconfigured resources.
When lambda takes action it pushes what it did and when it did to the slack channel which is monitored by security engineers.
Conclusion:
In conclusion, misconfiguration remains a significant threat to cloud security in 2023. It occurs due to human error and can result in unauthorized access to resources, potentially leading to data breaches and other security incidents. Organizations must understand the importance of preventing misconfiguration and adopt measures such as education and training, the principle of least privilege, monitoring and governance, encryption, and event-driven security. HBO Max provides an example of effective event-driven security architecture for detecting and remediating misconfigured resources in real time. By implementing these measures and learning from real-world examples of misconfiguration attacks, organizations can better protect themselves from cloud security failures and keep sensitive data secure.
